Intro

My name is Sergio Uncos and I am a Cybersecurity Professional with a total of +6 years of IT
experience and +3
years working in Information Security. I have a proven track record of success in
protecting systems and data from malicious actors and other cyber threats.
On this website, I will be sharing all my knowledge, experience, CTF walkthrough machines,
articles about Security Awareness, current working projects, and labs with the goal of
helping others stay safe online.
Technical Skills:
Operating Systems:
Windows & Linux environment management, Active Directory, Policy & procedures enforcing,
Virtualization (VirtualBox/VMWare), Hardening (CIS Benchmarks)
Security:
Security Assessments, OSINT (Open Source Intelligence), Networking TCP/IP, OWASP Web (Web
Application Security), SAST/DAST (Static and Dynamic Application Security Testing), Wireshark,
Kaspersky, Windows Firewall, iptables (Linux), Wazuh SIEM (Security Information and Event
Management, ELK Stack: Elasticsearch, Logstash,
Kibana), Metasploit, Nmap, Nessus, Rapid7 Nexpose, OpenVAS
Security Automation Tools::
Fortify, Snyk, SonarQube, SonarCloud, Checkov, OWASP ZAP (Zed Attack Proxy), Burp Suite, Nmap,
Nessus, Rapid7 Nexpose, OpenVAS
Cloud Computing (AWS):
IAM, Security Groups, VPC (Virtual Private Cloud), EC2 (Elastic Compute Cloud), Terraform
Containers:
Docker
Authentication and Identity Management:
Okta, Google Authenticator
Scripting Languages:
Python, Bash
Practice builds knowledge; knowledge builds confidence.
Work Experience
Latch, United States - Information Security Specialist
December 2023 - Present
- Security Infrastructure Management: Configuring and overseeing security tools, such as
intrusion
detection/prevention systems and endpoint protection solutions, to protect against cyber
threats.
- Access Control Administration: Implementing access controls and authentication mechanisms to
protect sensitive resources from unauthorized access.
- Risk Assessment & Vulnerability Management: Identifying and evaluating potential security
risks
and vulnerabilities within systems, networks, and processes.
- Incident Response Leadership: Developing and refining an incident response plan,
coordinating
with IT teams for rapid mitigation actions, and conducting post-incident analyses.
- Compliance & Audit Collaboration: Working with auditors to facilitate audits and ensure
compliance with regulatory requirements, reinforcing the organization's commitment to a
secure
and compliant IT environment.
This role demands a deep understanding of information security principles and the ability to
apply them in a dynamic, fast-paced environment. It involves not just preventing and
responding
to threats, but also fostering a culture of security awareness and resilience across the
organization.
Freelance, United States — SOC 2 Reviewer
November 2022 - Present
- Conducted comprehensive SOC 2 Type 2 compliance reviews of organization's policies,
procedures,
and
systems.
- Identified and reported compliance gaps and areas of non-compliance to stakeholders.
- Recommended improvements to controls and processes to meet SOC 2 Type 2 requirements.
- Collaborated with IT, security, and compliance teams to resolve compliance issues.
- Maintained detailed records of SOC 2 Type 2 compliance activities, including audit plans,
findings,
and recommendations.
- Ensured the organization met the highest standards for protecting their systems and data.
- Helped build trust with customers and stakeholders by demonstrating the organization's
commitment to
maintaining high levels of security and compliance.

Wazuh, Spain — IT Security Engineer
July 2022 - December 2022
- Successfully implement, tailor, provide assistance and manage the software product for new
and
existing global customers.
- Collect user feedback, recognize user demands, prerequisites and enterprise motivators for
mechanization and coordination resolutions.
- Deliver detailed and advanced technological demonstrations for clients, collaborators and
potential
customers.
- Educate users to empower their future self-reliant utilization and setup.
- Guide and instruct security engineers, security operations teams and emergency responders.
EdgeUno, United States — Security Engineer
July 2021 - July 2022
- Implemented, enforced, and refined information security policies using industry-standard
frameworks
like NIST and CIS for comprehensive protection.
- Conducted vulnerability management and regular penetration testing for EdgeUno and clients
using
tools like Nessus, Nmap, and Burp Suite.
- Operated and maintained the SIEM platform and utilized data security and compliance tools,
ensuring
compliance with GDPR and other regulatory standards.
- Responded to incidents, conducted investigations, and improved enterprise security through
customization and automation using self-developed tools with Python.
- Deployed and managed corporate security systems for robust protection using technologies
like
firewalls, VPNs, and IDS/IPS.
- Conducted research and evaluation to develop product security planning and identify
potential
risks,
leveraging threat intelligence feeds and security advisories.
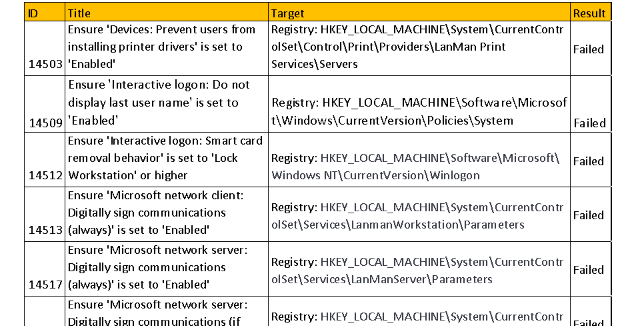
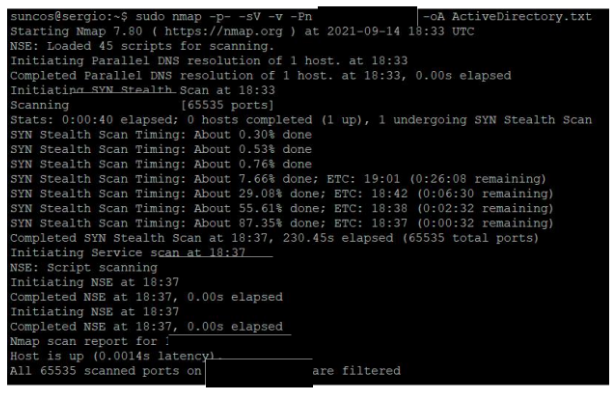
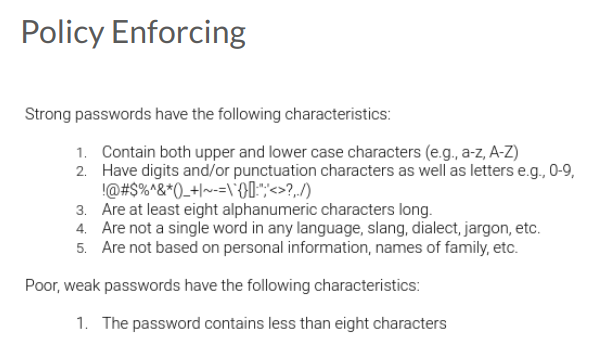
Novared, Argentina — Information Security Analyst
November 2020 - July 2021
- Managed, configured, and supported McAfee platforms (ePO, DLP, ATD, ENS, MVISION) and
Tenable
for
incident reports and alerts about discovered vulnerabilities, ensuring comprehensive
security.
- Escalated product issues to third-party vendors and suppliers for swift resolution,
minimizing
downtime.
- Developed reports with useful information, including the performance of installed products
on
customers.
- Conducted root cause analysis of incidents within labs and tested new configurations,
ensuring
continuous improvement of products and services.
- Maintained awareness of emerging threats and technologies and evaluated new products and
services to
enhance security capabilities.
About
I have a strong passion for assisting others to achieve their goals and also offering support and
coaching. My devotion to learning allowed me to become fluent in English, Portuguese,
and Spanish.
I do consider myself as a knowledge seeker, an explorer. Based on this, there is a growing list
of books that have helped me during my career and strongly recommend:
- Atomic Habits - James Clear
- The Power of Habits - Charles Duhigg
- Make Your Bed - William H. McRaven
- Enfócate - Cal Newport
- The Four Agreements - Miguel Ángel Ruiz Macías
- The Life-Changing Magic of Tidying Up - Marie Kondo
- Limitless - Jim Kwik
Recognitions
AWS
(Certified Cloud Practitioner)
Open
Source
Vulnerability Management Lecture
C1 English Level
Contact
This is where you can get in touch with me! I'm always happy to hear from you, whether you have a
question, a comment, or just want to say hello.
I'm always up for a good conversation. Whether you have a question about my work, want to share your
own thoughts and ideas, or just need someone to vent to, I'm here for you.
So go ahead and drop me a line! I'm looking forward to hearing from you.
Tools
Here you can find a collection of tools that I use on a daily basis and which are highly recommended.
IP & URL Reputation
Malware analysis
Simulate browser
SAST - DAST
- Snyk - Opensource tool for scanning your
projects and code. It does provide a VSC extension to solve issues during development stage.
- HostedScan - An online OWASP Zap ready
to use for DAST
- Checkov - IaC scanner, more reliable
than Snyk during IaC code scanning
- SonarCloud/SonarQube - Its main focus
is SAST and SCA analysis, but it can also be used for DAST and IAST because it integrates
with several tools.





